So I’m sure you’ve seen the alert that BSides Las Vegas is cancelled this year, you know, due to that thing that’s going around.
I have zero inside information, but I can’t imagine a scenario where this doesn’t play into the decision process for DEFCON and BlackHat, since it’s the same location during the same week. While I haven’t cancelled my hotel booking yet, it’s looking more and more likely.
I’m sad about this.
Mood…

Monday night check-in event announced…
See website for details.
Fun with Payphones, part 1
So I scored an old payphone. My “vintage replica” just wasn’t cutting it anymore.
It appears to be a Western Electric single-slot 1C from May of 1977.

Decent cosmetic condition, but looks aren’t the reason I bought it. I bought it to learn, play, restore, and maybe even modify it.
It didn’t come with keys — this is problem #1.
There’s a reason these things stayed in service so long, and it’s not just because cellphones were invented and eventually became ubiquitous and disposable. It’s also because they were seriously armored and indestructable. Picking these locks when they’re in good shape is no joke. In fact, I found the restricted Bell document that shows what to do when you no longer have the key to the vault door (the shiny square door at the bottom) — basically you use a circle template and drill through the door so that you have direct access to the latch bolts internally. Then you replace the door and the lock assembly with one which has keys.
The problem is, step one in that process is “remove the cover assembly.” Which is also locked. So what if I ALSO don’t have keys to the cover assembly? Well, I guess I could maybe drill that lock out — BUT I found another tutorial that indicates that with 8-15 minutes of tapping with a dowel and hammer, you basically nudge the four screws securing that lock assembly out from the inside.
It looks like that would have to happen anyway, because these locks looks like shit, and might not be pickable even by a TOOOL expert on a good day.


Fortunately, replacement vault doors, coin vaults and lock assemblies with keys are available on eBay, so eventually this project may find itself nudged further along. I’ll update you.
Another successful meeting on the books.
Only a couple members could make tonight’s meeting, but it was a positive meeting anyway. I was working on my Vic-20 recovery when Kevin arrived, and we pretty quickly ended up in a conversation about Zeek. He needs to master it for work, and I need to master it just because. I found a lab from FAU that might be helpful. Here’s the link:
http://ce.sc.edu/cyberinfra/docs/workshop/Zeek_Lab_Series.pdf
We did a bit of research on network taps, and settled on Great Scott Gadgets’ Lan Tap Pro (or, if you’re cheap and handy like me, the Throwing Star Lan Tap Kit). both are passive LAN taps, and will pipe all traffic that passes through them into your Zeek, Snort or other IDS box.
We’re looking forward into the new year and planning some exciting talks and presentations. Maybe we’ll talk about Zeek in February if we’re ready, and Dan wants to talk about social engineering research tools, possibly in March.
Next meeting is Monday February 24. I hope you can make it.
Site move
Today I migrated the DC540 website to an overseas VPS. Somehow an overseas VPS, with just 2GB of RAM, responds faster by multitudes than shared hosting at Hostgator. I guess Hostgator has reached maximum oversubscription. Please let me know how YOU experience the website, and let me know if I missed any bugs. Took me longer than I should have to get the events plugin working, for stupid configuration reasons that I am too proud to admit.
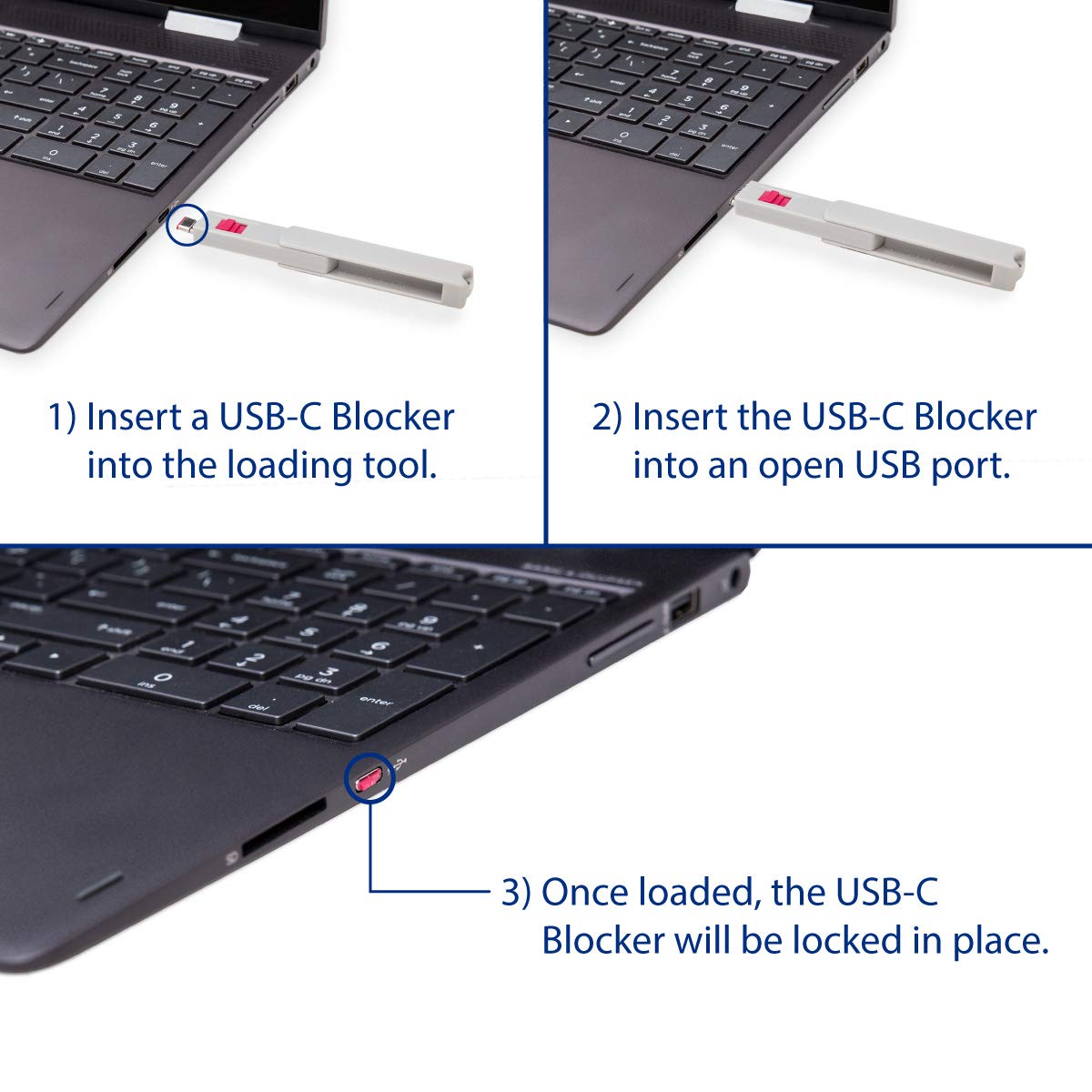
USB-C physical port blockers…
Didn’t know this existed. Sounds like a great thing for potentially hostile locations, cons, etc. Take your macbook, lock all the ports, don’t worry about somebody using USBKiller or BadUSB on you.

Holy Crap, It’s 2020!
Several people indicated being unavailable on the fourth Monday in January. Options: 4th Monday anyway, 3rd Monday (MLK day), some other day. I’ll pencil in 4th Monday anyway until we achieve consensus.
Apache, filebeat and Graylog – Oh My
I’ve been getting notices from one of my more popular WordPress sites of an increasing number of attempts to login lately. Compared to my other sites, this one feels like it’s being targeted for some reason. Normally I don’t pay a whole lot of attention to Apache logs unless I’m troubleshooting something, but I felt like ignoring this would be a missed opportunity.
The site is hosted on a shared site out in the wild. I don’t have full access to the server, but the vendor is kind enough to deposit apache logs into a known location on a regular basis.
So I spun up a Graylog instance at home, setup an automated rsync to suck down the logs, and then used filebeat with a logstash output to pipe them into Graylog for me. At some point I might set up a real SIEM (maybe SIEMonster’s community edition?) to do a bit of threat intel for me, but for now it’s a good pull this morning to have the logs for 20-30 websites sucked into my Graylog VM as a starter.
It’s a two-pot coffee day today.
The exercise ended up pulling in about 3 million log lines, and now I can easily visualize a history of what these ass-monkeys did on my hosting server.
FOLLOWUP: Yeah, turns out they were attracted to the WordPress by the unsecured Wiki hiding underneath. On 11/6, I upgraded mediawiki, and apparently missed turning off registrations. Since then, I’ve had 55,000 new users on the Wiki, and over 60,000 page edits (new pages, spam vandalism, etc). It was relatively easy to clean up after, but they were really having their way with that site.
I suspect the brute-forcing is going on especially hard today because they think nobody’s watching on a holiday weekend. BITCH I’M ALWAYS WATCHING.
The electronics for the LED marquees arrived today…
As a reminder, anyone who wants one of these should bring $15 to the December 16 meeting. You’re welcome to assemble them with the group during the meeting, or take it home and do it later. It’s a pretty easy assembly, just five wires to solder to the Wemos and the LED assembly, and then apply some code to make it do its magic.