It’s not even an abundance of caution. After reading the latest from WHO and CDC, it’s just common sense. Stay safe, y’all. We’ll get together when thing settles down.
Fun with Payphones, part 1
So I scored an old payphone. My “vintage replica” just wasn’t cutting it anymore.
It appears to be a Western Electric single-slot 1C from May of 1977.

Decent cosmetic condition, but looks aren’t the reason I bought it. I bought it to learn, play, restore, and maybe even modify it.
It didn’t come with keys — this is problem #1.
There’s a reason these things stayed in service so long, and it’s not just because cellphones were invented and eventually became ubiquitous and disposable. It’s also because they were seriously armored and indestructable. Picking these locks when they’re in good shape is no joke. In fact, I found the restricted Bell document that shows what to do when you no longer have the key to the vault door (the shiny square door at the bottom) — basically you use a circle template and drill through the door so that you have direct access to the latch bolts internally. Then you replace the door and the lock assembly with one which has keys.
The problem is, step one in that process is “remove the cover assembly.” Which is also locked. So what if I ALSO don’t have keys to the cover assembly? Well, I guess I could maybe drill that lock out — BUT I found another tutorial that indicates that with 8-15 minutes of tapping with a dowel and hammer, you basically nudge the four screws securing that lock assembly out from the inside.
It looks like that would have to happen anyway, because these locks looks like shit, and might not be pickable even by a TOOOL expert on a good day.


Fortunately, replacement vault doors, coin vaults and lock assemblies with keys are available on eBay, so eventually this project may find itself nudged further along. I’ll update you.
February Meeting cancelled!
Sorry folks, I had to cancel hosting the February meetup. Heading out to Vegas (I know, not even Defcon season!) to help my mom recover from cancer surgery. You’re welcome to meetup on your own at Glory Days or wherever if you like. Please talk amongst yourselves. 🙂
DC540 Defcon Meetup – Stone Ridge, VA – March 2020
Hey folks, the February meetup has been cancelled due to family emergency travel. Sorry about that. Setting up the March meeting now, fourth Monday, March 23, 2020. More info will be added before then.
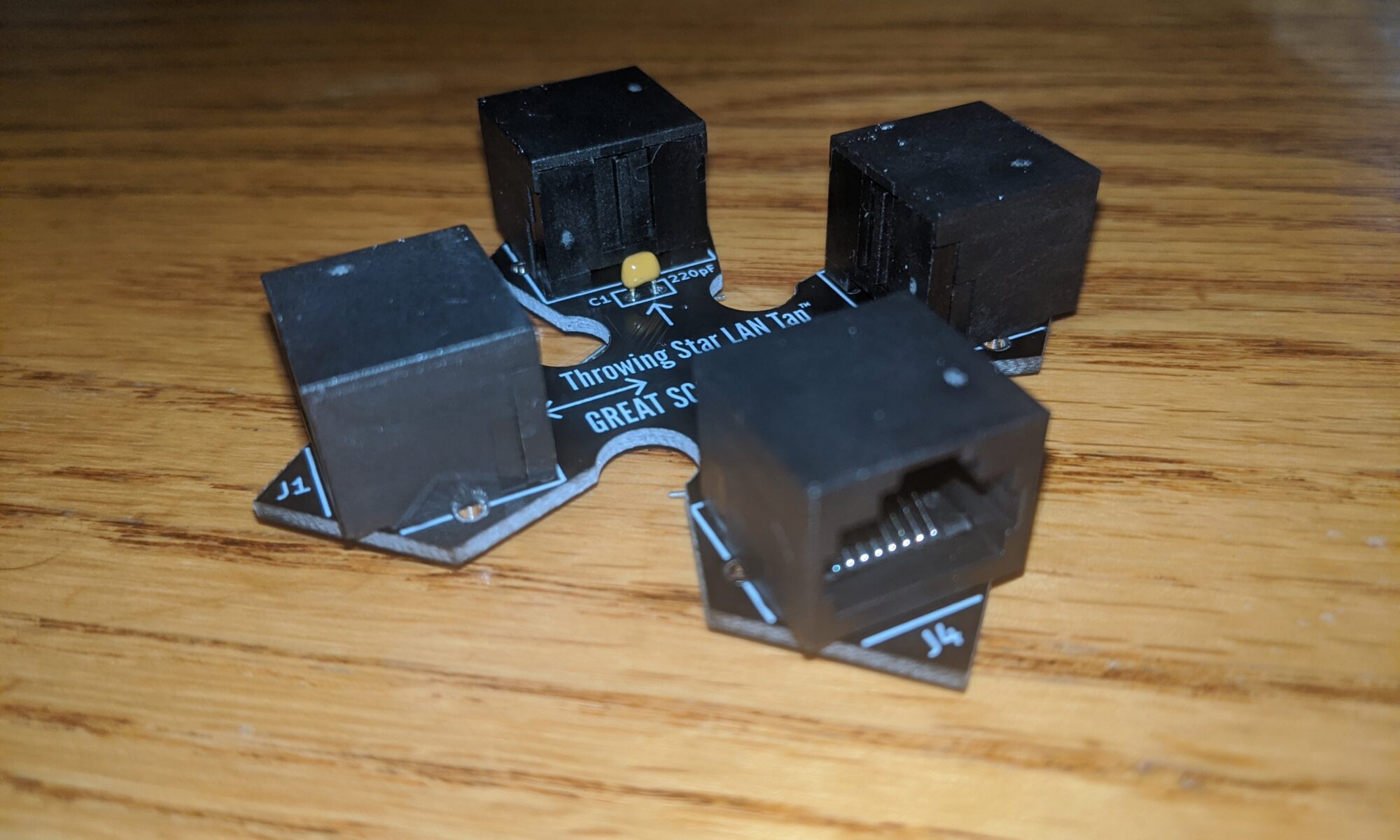
$15 Lan Tap? You’re joking, right?
During the last meeting, we were discussing Zeek (formerly Bro) and narrowing down choices for sniffing accessories (tap vs span port). We settled on the Great Scott Gadgets lan taps. The pro version is enclosed and complete for $40, and the Throwing Star version is in kit form and just $15. Because I’m (a) cheap, (b) addicted to flux fumes, and (c) a ninja, I opted for the throwing star. I just slapped it together in about ten minutes, and it seems to be working just fine.


Another successful meeting on the books.
Only a couple members could make tonight’s meeting, but it was a positive meeting anyway. I was working on my Vic-20 recovery when Kevin arrived, and we pretty quickly ended up in a conversation about Zeek. He needs to master it for work, and I need to master it just because. I found a lab from FAU that might be helpful. Here’s the link:
http://ce.sc.edu/cyberinfra/docs/workshop/Zeek_Lab_Series.pdf
We did a bit of research on network taps, and settled on Great Scott Gadgets’ Lan Tap Pro (or, if you’re cheap and handy like me, the Throwing Star Lan Tap Kit). both are passive LAN taps, and will pipe all traffic that passes through them into your Zeek, Snort or other IDS box.
We’re looking forward into the new year and planning some exciting talks and presentations. Maybe we’ll talk about Zeek in February if we’re ready, and Dan wants to talk about social engineering research tools, possibly in March.
Next meeting is Monday February 24. I hope you can make it.
Site move
Today I migrated the DC540 website to an overseas VPS. Somehow an overseas VPS, with just 2GB of RAM, responds faster by multitudes than shared hosting at Hostgator. I guess Hostgator has reached maximum oversubscription. Please let me know how YOU experience the website, and let me know if I missed any bugs. Took me longer than I should have to get the events plugin working, for stupid configuration reasons that I am too proud to admit.
DC540 January Meetup
Let’s try this again —
Several regulars can’t make January 27.
I can’t make January 20, conflicting meeting.
How do any stragglers feel about January 21 (Tuesday)?
Thoughts?
TIL about john the ripper and trigraph frequencies.
I have an assignment to crack an Office password for a document. I have tried using john and hashcat with several large wordlists, and had no luck, so I decided to go all-in and just leave a Kali instance running john in incremental (brute force) mode for “as long as it takes.” It’s been two days so far.
I have it running within ‘screen’ so that I can occasionally login to the system remotely to check progress without risk of losing it. I was excited at one point yesterday seeing that it was in the middle of checking seven-character passwords, but then I checked back later and it was checking six-character passwords. This morning, five. I wanted to understand — I assumed (without doing a deep dive on the mechanics) that it would just go literally incrementally. aaaaa, aaaab, aaaac, etc. That was an incorrect assumption.
John’s incremental mode actually operates on “trigraph frequencies.” While I understand the concept of trigraph frequencies (certain sets of three characters occur more frequently than others, and this can help with decryption efforts, I have my doubts as to whether this helps in cracking passwords. Passwords aren’t always natural speech, after all.
Anyhow, it’s been running for two days now, and I’ll post about it again when it’s done just to give an idea of whether it’s successful, and if so, how long it took vs the complexity of the password.
If anyone else wants to try using similar or other methods, let me know, and I’ll send you the hash (generated by office2john). No, I can’t send you the actual document. That would be unethical.