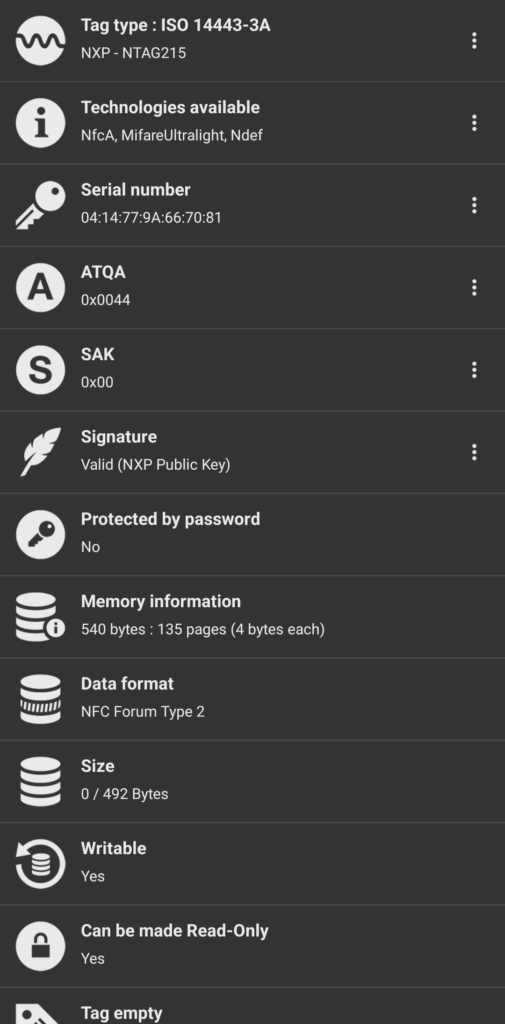
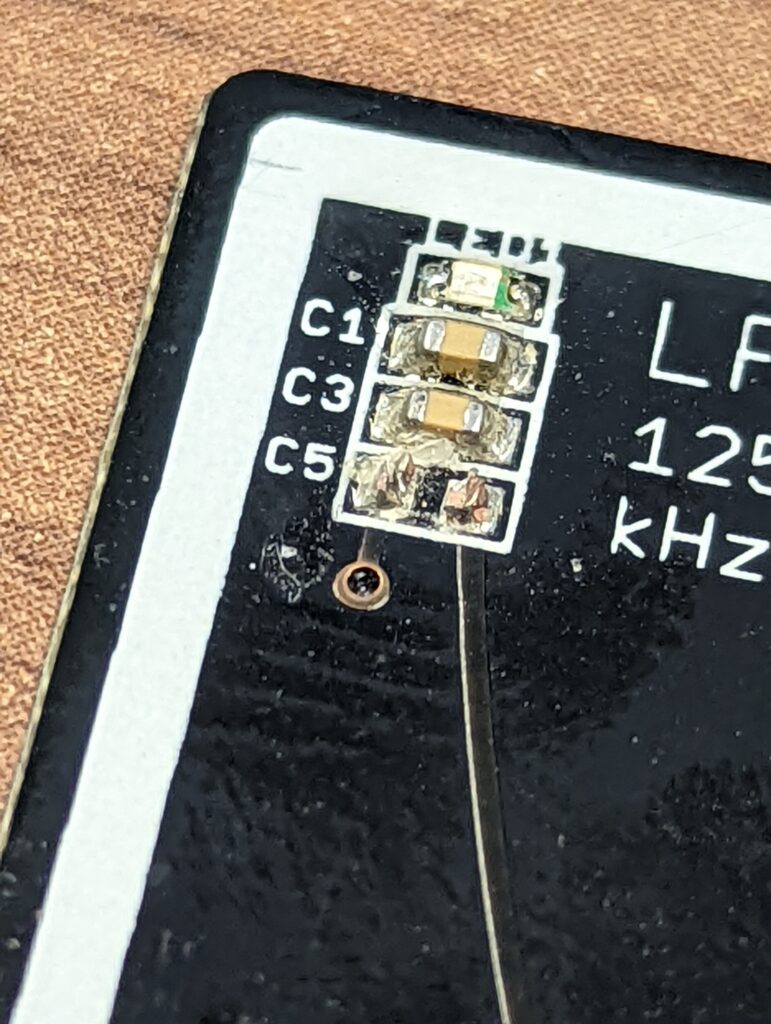
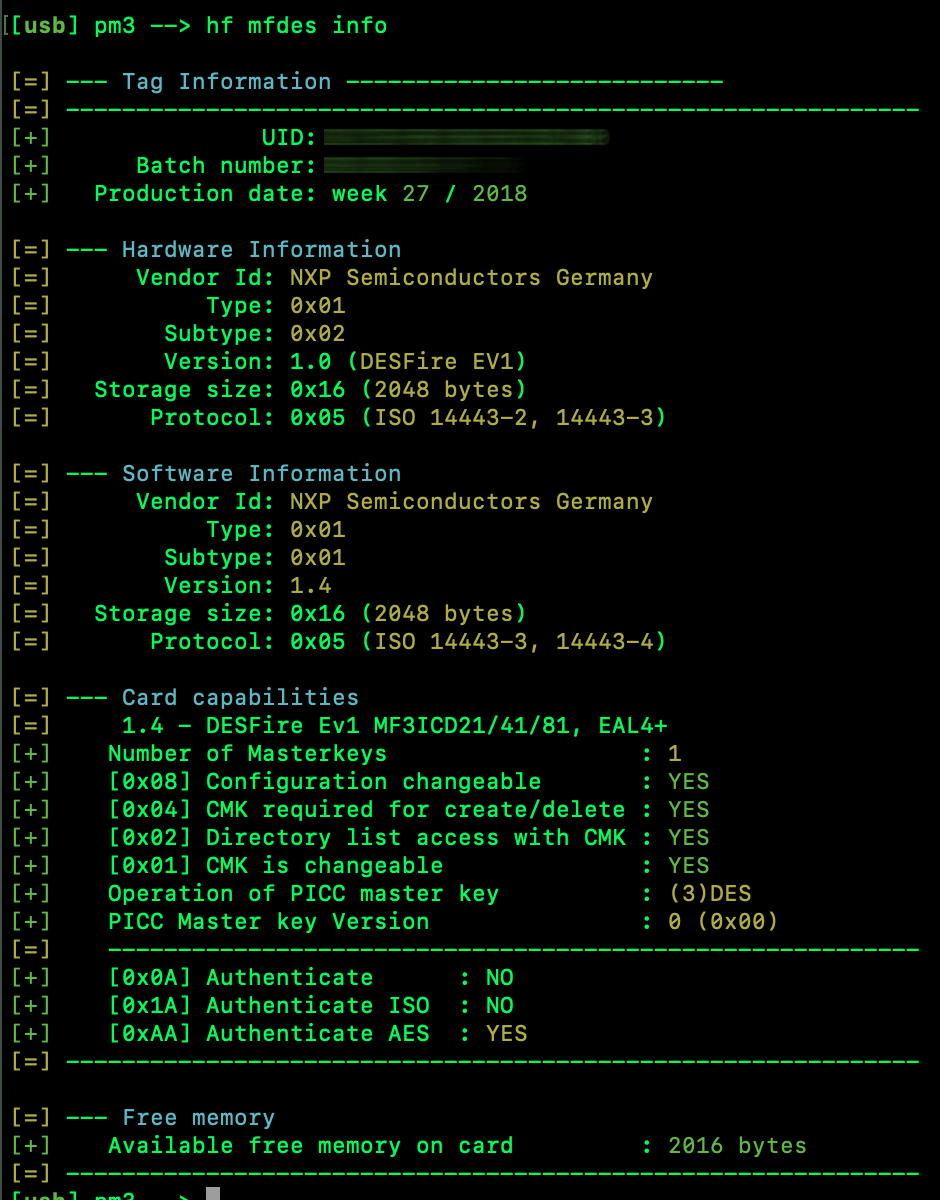
So some years ago I picked up a Fargo DTC400e id badge printer at auction. It was cheap, and something I wanted to fool around with. I had already been recreationally fooling around with magstripe and RFID cards, it just seems like a natural progression of interests.
A recent meeting revitalized my interest. There’s a thing the group wants to do and it might come in handy. I was all set to buy a dye sublimation printer and go down that route, either printing direct to cards or to vinyl transfer which would then be applied to the cards, when one of the members mentioned “id card printer” and them I remembered that I had this thing buried in a bin somewhere. I had futzed with it in the past, but did not get good results. Might have been the wrong kind of card to print on, might have been an aged ribbon, I abandoned it back then because “overcome by events” and lack of interest, but here I am looking into it again.
Here’s what I’ve found so far:
- The DTC400e was a decent card printer in its day. It was likely expensive in its day. Its day has passed. The ribbon cartridges appear to be discontinued, it’s likely that anything I’d be able to find in stock would be old stock. Someone is selling some on ebay that was manufactured in 2011/2012. I don’t think it was meant to last that long.
- Modern dedicated id badge printers are expensive. The cheapest I’ve managed to find is a very low-end $400 model that only prints on one side. The DTC400e can print on both sides. Most comparable models are over $1,000. For far less than that I could get a decent dedicated dye sublimation printer and do much more than ID cards with it.
- The DTC400e is used via the Fargo Workbench software. It’s so old that there are no Windows 10 drivers for it available. I even had quite a bit of difficulty finding the Windows 7 drivers for it. Eventually I did, and end up performing a staggering series of sysadmin feats of strength just to get to test mode:
- Installing Windows 7 via ISO didn’t recognize NICs in my HP ProOne600 G2 All-In-One PCs that I use for group stuff.
- Installing the NIC drivers after that resulted in an inability to install the workbench software due to dead Windows Update functionality on that obsolete Windows.
- I had avoided deploying Win7 from my FOG installation because I had broken my FOG installation in 2023 for some reason and didn’t want the extra steps of making that work again.
- But that’s what I ended up doing. Fixed FOG and deployed a Win7 image I had saved a few years ago. Fargo Workbench installed just fine on that, the DTC400e drivers I found installed fine, and now I have a valid test platform.
- Is it worth buying a new ribbon for somewhere between $60 and $150? Maybe. If nothing else, just for the experience. I found a YMCFOK ribbon slated to work with this unit for $82. Mostly I had been finding YMCOK ribbons, which would be fine. But the F is exciting:
- Y=Yellow
- M=Magenta
- C=Cyan
- F=Fluorescing! (security layer only visible with UV light)
- O=Clear protective overlay
- K=Black Resin
So that’s where I am now. The printer is reachable by the software on a reincarnated Win7 build from quite some time ago. I’m about to pull the trigger on a new ribbon. And a couple of us are taking a dye sublimation class this evening in case it goes that direction.