Baab will be in the air during this evening’s weekly meetup, returning from LV. But nothing at all is stopping the rest of you from holding a Discord meetup. We’ve picked up a bunch of new friends recently, both from Kevin’s RE courses and from our many, many in-person Defcon interactions.
The normal time is 1830 Eastern. The Discord perma-invite is on the dc540.org website.
We meet in the Monday Meetup voice channel. We are welcoming to new members, we like to get to know people this way before attending an in-person gathering with us.
Monday 6/14 Meeting is In-Person
OK, Actually it will be Hybrid. We want to be inclusive to those who can’t make it out. We’ll be talking about badge planning, and I’ll give a demo of PCB design and how to build a badge in KiCad, from a blank slate to fabrication. You can put your filthy grubby hands on the early prototypes of the badge we hope to release at “summer camp” this year.
Weather looks good for a backyard meetup. I’ll see if I can bring a large-ish screen out to the table so everybody doesn’t have to crowd around my laptop. And I’ll stream the screen in the Discord so everyone can see it.
Prepping for 2021’s first in-person meetup
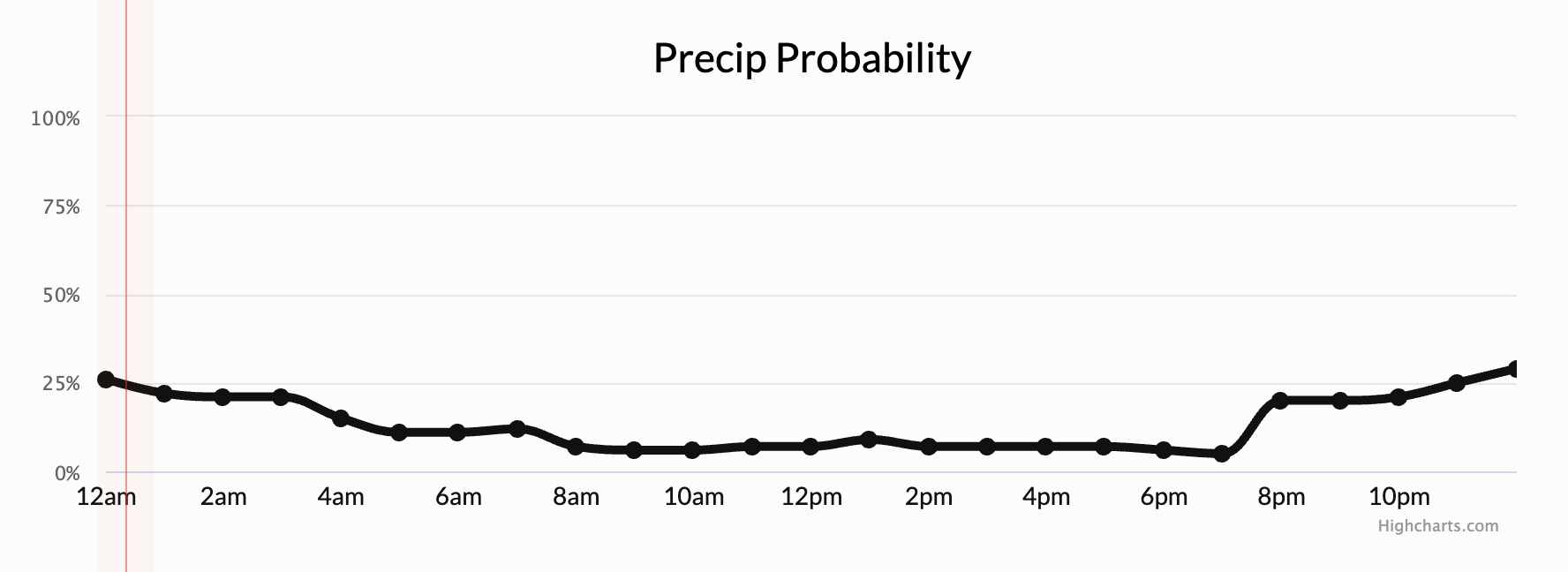
Next week’s meetup is slated to be DC540’s first in-person meetup this year. We decided to schedule the in-person meetup in the backyard. Since we made that decision, the CDC advised that vaccinated people should be able to gather indoors maskless. But we’re fine with outdoors. Especially since, when we scheduled it, it was looking like it might rain Monday evening, but since then the probability has decreased steadily. Looking very promising now.
We’ll have enough Raspberry Pi Pico microcontrollers to go around, I’m trying to pre-solder a bunch of headers so you don’t have to waste time soldering and you can get started right on deploying programs onto it. I’ll also have some breadboards and LEDs to play with if you’re so inclined. If you want to be prepared to play with that, install Thonny on your laptop and consider bringing a standard MicroUSB cable. MicroPython is WAY easier to get started with on the Pico than C. Plug it in with Thonny running, Thonny will prompt you to flash MicroPython firmware onto it, and then you can just save your python programs straight to the USB-connected Pico and run them. Easy as Pi.

DC540 Workspace Tour
I’ve been wanting to slap this together for a while. Since we have so many members who have never seen the space (thanks Covid!), I thought I’d give you a taste.
2020-10-05 DC540 Monday Check-In
Nice DC540 meetup on Discord tonight. Topics ranged from #badgelife to RFID and biohacking, to slavery and oppression, to pentesting and red team methodology and mindset, among others. Looking forward to creating some content in these areas!
Monday DC540 Discord Check-in
Progress is being made, we’re all fulfilling our dreams in exotic ways. Tune in 6:30p tomorrow as we drink away our frustrations and verbally abuse one another.
March Meeting Cancelled
It’s not even an abundance of caution. After reading the latest from WHO and CDC, it’s just common sense. Stay safe, y’all. We’ll get together when thing settles down.
February Meeting cancelled!
Sorry folks, I had to cancel hosting the February meetup. Heading out to Vegas (I know, not even Defcon season!) to help my mom recover from cancer surgery. You’re welcome to meetup on your own at Glory Days or wherever if you like. Please talk amongst yourselves. 🙂
December Meeting update…
Things are rolling right along for December’s meeting. I hope to see a bunch of you on the 16th.
- I’ve got a healthy smattering of Kali and ParrotOS workstations on the long table ready for anyone who wants to do actual pentesting against the CTF server. (These were the HP All-In-Ones I picked up at the auction.)
- The CDC book will be one door prize/raffle for one lucky winner, and I will also have a few decks of “Backdoors and Breaches,” a tabletop card-based game for simulating incident response using a D20 for other winners.
- As I mentioned before, the LED Marquee parts kits are all here ($15 a set), and I built and tested one. It’s been up and running in my family room for a couple of weeks now. If you want to assemble one at the meeting, it’s super-easy, and if you want it programmed as well, I’ll leave the choice up to you whether you want me to push the programming from my Arduino IDE on my laptop, or if you’d rather go through the process of setting up Arduino yourself, for the learning experiences. There are a number of dependencies and modifications that need to be made, more than I’ve had to do in any other Arduino project. Most of them are well-documented, and some are just common-sense fixes, I trust all of you are capable of figuring it out. It’s just a matter of do you want to go home with a working device or a challenge. 🙂
I mentioned this on Twitter, but not all of you follow Twitter — I picked up the “Crash Course Electronics & PCB Design” course on Udemy over Black Friday weekend for just $10. I can’t say enough good things about it. I have a reasonable enough basic understanding of electronics to get by on mimicry and duplication with minor troubleshooting, but I’ve always wanted a deeper understanding and more foundational knowledge. This 100-hour course, taught patiently by Andre Lamothe, is really hitting the mark.
I guess the best way to characterize it is, come for the PCB design, stay for the best approach to electronics foundational knowledge I’ve seen yet. I was going to skip ahead to the PCB design part, but I’m learning and enjoying the electronics portion so much that I haven’t been able to pull myself away. Already I’ve added a few more things to my wishlist (a signal generator, a set of thru-hole diodes, etc.) and acquired a renewed sense of vigor and enthusiasm for my portable payphone project, which fell by the wayside in the old house when I ran into issues trying to power it properly. Exciting times indeed. It’s one thing being able to troubleshoot a circuit by trial and error. It’s another thing to understand the math and theory behind it and be able to make it right — or even make it better.
Be sure to register for the meeting so that I can be sure to have enough beer chairs for everyone.
The LAB comes alive!
So I happened upon an auction for a collection of HP All-In-One PCs. I’ve always thought they were great general purpose solutions for classroom, lab, specific location browser use. Not what any PC fetishist would want, but fine for group use or general use purposes.
The price was right, so I picked them up, not knowing the complete specs, with only pictures and a “tested and working” claim attached to them.
I fired the first one up during the November meeting the other night. It booted into Windows, with an enterprise login screen for a medical group — brilliant, they sold medical PCs without wiping the hard drives. Mucked around with the BIOS settings so that I could boot Ubuntu to determine the specs of the machine without opening it up, found out it had bitlocker, which didn’t like me mucking with BIOS settings.
Tried to install Kali via Fog, something was busted in my Fog installation, so I just installed Ubuntu from a USB. It turns out they have an i5 4590s quad-core in them, along with 8GB RAM and a 500GD HDD. 4x USB 3.0 ports, 2x USB 2.0 ports. Gigabit ethernet and Wifi built-in. Not too shabby, glad I picked up this auction.
So the other night, I fixed Fog (firewalld was blocking TFTP), and deployed Kali. Updated and re-captured the image so that the future builds would be more up-to-date, then imaged the second unit this morning. Imaging a new unit just takes two minutes when connected via Gig-E.
Late last night I noticed one showed a CD in the drive. Popped the tray, and what do I find but a CD, labeled by a medical services vendor, with the attached label on it.
The file on the CD was a PDF file. The file name was the patient’s full name in last, first middle format.
It took just a minute or to to create a file with every possible date for the last century, seconds to normalize the password hash so that security tools could use it, and then just seconds to run a brute force tool against the hash using the wordlist I created. Within just a few minutes of discovering the CD, I was able to view a patient’s FULL MEDICAL HISTORY.
Some lessons here:
1) DON’T leave sensitive media in PCs that are going up for auction or to be “destroyed.” Never trust that process to someone else. Remove ALL media — USB, CD, hard drives, etc. Wipe/destroy them separately.
2) DON’T put a label on something telling whoever has possession of it the exact format of a password — it really narrows things down and makes it much easier for us to “guess” it.
3) DON’T make the filename the person’s full name.
4) DON’T use DOB as a password field. It’s absolutely not complex enough. Make it a long password and hand that piece of paper to them separately, or make it available in your highly-secured medical portal.