…pieces of cultural apparel…
(and SDRs)
(and Pi/Arduinos)
(and solder irons)
(and storage bins)
(and hotel cards)
…pieces of cultural apparel…
(and SDRs)
(and Pi/Arduinos)
(and solder irons)
(and storage bins)
(and hotel cards)
How many of you are in on the GoCube Kickstarter? GoCube is a Rubik’s Cube on steroids. Orientation sensors, move transmission via Bluetooth, stickerless with speedcube mechanics.
I’m an old-school cubist. I learned the old way with the old patterns. I’m a sub-two-minute solver on a good day. With this invention, I’m willing to learn the new speedcubing methodologies and get my solve time down lower.
This book arrived at my doorstep yesterday. Color me excited. $12 something at Walmart, go figure. He goes way into Chinese factories, manufacturing and the supply chain before getting into the hacking part of it. Exciting if you’ve got some hardware ideas in your head.

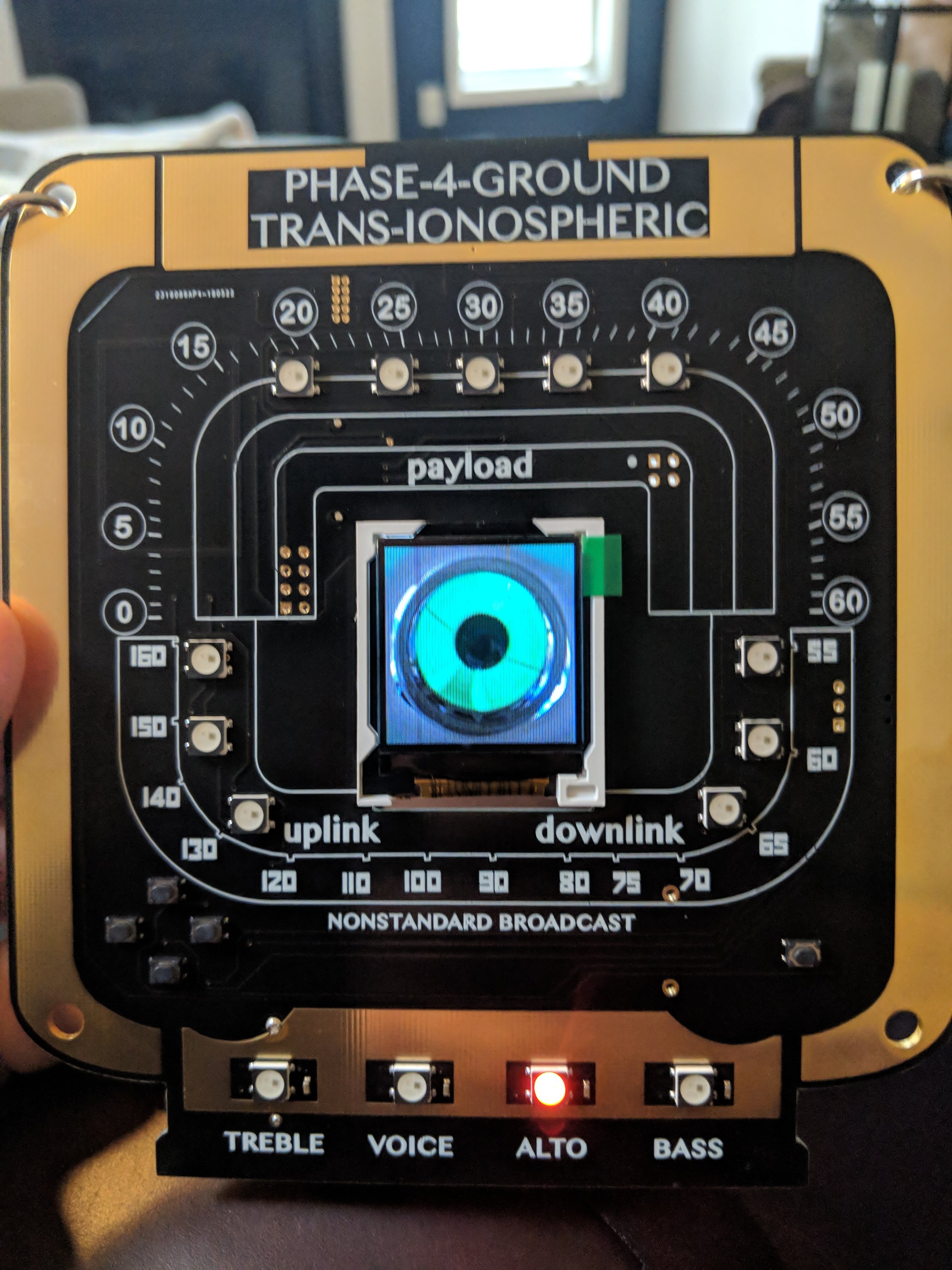
This one is the Phase 4 Ground Trans-Ionospheric Badge, and it’s got a ton of cute visualizations on the screen, games, customizations (name and call sign), and even some actual contact logging/QSO functionality. Another one where the maker decided to undercut the eBay upsellers by doing another run (or maybe there were just leftovers, who knows?). Maybe this trend will keep the badge-scalpers at bay, and keep the prices down to “moderately outrageous” for those of us who can’t seem to say no.
I wish I could tell you which was my favorite of all the badges out there, but I can’t compare function to form in an articulable manner.
You’re doing a great job with your RSVPs so far. I’ve got 8 members coming to the first meeting last time I looked. If you haven’t RSVPd, and you plan to come, you should probably RSVP via Meetup (or directly if you don’t use Meetup), because the room doesn’t have unlimited capacity. Also helps for planning. Also, we’re still not listed on the official Defcon groups page. When that happens, a few more slots may fill up.
I should mention that there will be swag.
I expect there will also be a lockpicking station. Maybe a Proxmark to play with.
If anyone is interested in helping behind the scenes, let’s meet up before the meeting, I’d love to hear your ideas.
Also, please take the poll I posted a few days ago if you haven’t already. It will help guide meeting content.

I had a serendipitous experience last year. The wife and I decided to celebrate a big round anniversary and a big round birthday by embarking on a rather ambitious journey. We drove to St. Louis for the eclipse, then to Burning Man. We got there a few days early to help out with “build week.” The Burning Man stories are for another time and place, but at some point after the event opened officially, I noticed that a camp schedule was posted (we camped in a village of several camps, with a large group of mostly DC area burners). While perusing the schedule, I noticed that there was a lockpicking class on the schedule. I asked the leader of that camp about it, and he replied, “oh yeah, there was going to be a class, but the guy who teaches it couldn’t make the Burn this year.” Excitedly, I asked if his equipment made it without him (it had) and volunteered to teach the class.
Fast forward to class time. I figured one or two people would wander by, so I spread out the backpack full of labeled progressive lock cylinders (1-pin through 5-pin) and the other oddball cylinders and locks on a table with some chairs near the front of our camp and sat and started playing. One or two campmates came to keep me company and play along. It didn’t take long for people to start showing up, and soon the table was crowded. I’d like to say I gave them brilliant insights and harrowing demonstrations of technique, but all I really did was explain how pin tumblers work, and a general demonstration on how to use the tension wrench with just the right amount of pressure in hopefully the correct direction, and boy were they off! The table was aflutter with people shuffling cylinders around, saying “I’m done with 1, is there another 2 free?” “I’m up to 4 already!” Fast forward an hour or three (burner time is a bit fuzzy) and some 20-30 people or so (counting burners is also a bit fuzzy) successfully passed their first lockpicking class. Nobody failed, nobody gave up.
I still haven’t had a chance to thank the guy who didn’t show up. I think he’s part of TOOOL DC, may have dated one of the burners in the camp at some point or something (yeah, facts are fuzzy out there too). I was hoping to track him down at Defcon this year and thank him, but I didn’t manage to get around to it. Hell, there’s always next year.

Answer honestly, as it may affect the content of the meetups.
[democracy id=”2″]
Just a reminder that attending conferences, security group meetings, and similar activities can count toward continuing education credits for maintaining certifications.
I picked up CEH last April, and thanks in a large part to attending DEFCON twice and BSidesLV once, I’ve already got 89 credits toward the 120 required for maintaining my certification..
Over the winter, I intend to take on OSCP. What certs to you folks have?
Here are the activities that qualify as continuing education credits for CEH:
Better late than never. I think this one was released in time for subscribers to assemble it before Defcon. I slapped this together over the weekend. About the simplest project you can imagine. The switches turn the individual LEDs on, and the LEDs each have either a slow transition or fast transition IC built-in. The resistors are purely for decoration. It’s pretty and blinky, so I can’t complain.
The kit also came with a MicroPython PyBoard to experiment with. Going to have to steal some time to play with it, it really sounds like a lot of fun.

I was excited to pick up the new Proxmark 3 RDV4 from its Kickstarter, before the official, far more expensive release at Defcon 26. I’d been playing with it since I got it, cloned my office entry HID card, and tried out a couple of the Android apps to run it.
There are two Android apps that I’m aware of. Walrus is the one that seems promising to me. It leverages the ability to read, write and simulate (playback) RFID cards native to the Proxmark, and supposedly a feature under development is to brute force readers using bulk-collected tags. Sounds like a fun tool for physical pentesters. Collect cards in a crowded elevator, then try to get into offices using the cards you’ve collected. I haven’t checked for an update since downloading the software, so I have no idea whether it’s been implemented yet. The other one, AndProx, is a standard Proxmark CLI, and I’m not much for typing on phones. It’ll work in a pinch, but I prefer my trusty Macbook for that. Also, it didn’t seem to recognize the Proxmark from my phone. Maybe I need an OTG cable.
I picked up some keyfob tags on Amazon, because I have this annoying habit of forgetting my work card every once in a while and having to borrow a temporary card from the receptionist, and I figure if I have one on the same ring as my car keys it’ll be far less likely that I’ll leave it at home (or in the car). However, my RFID tag knowledge isn’t super deep, and apparently just looking for T5577 cards isn’t good enough. They read as “Indala” in the Proxmark, and I’m unable to clone my HID card to them as I could with the included Proxgrind card, or other random cards in my collection.
So I looked a little closer this time, and ordered another set of fobs that one reviewer claims he was able to clone HID with. Science is all trial and error, right?
If you’re considering getting a Proxmark, I’ll share a couple of experiences. Trying to update the bootloader and firmware from a Linux VM was problematic. The update hung and bricked the Proxmark. This was easily fixed by holding down the button on the unit while powering it up, and while re-uploading the bootloader and firmware directly from MacOS. If you get weird command errors, it’s because your client and firmware versions are out of sync. Once everything’s in sync, it’s like clockwork.
Side note: I’m getting to be known as “that guy” at work. A coworker asked me if I could pick tubular locks today. Gotta dig out my tubular pick set to bring in tomorrow. He wants to replace a drive in a locked drive array and doesn’t know where the key is.
Indala Update 2018-09-09: I somehow managed to get the “Indala” card to work. Hints from iceman gave me confidence that the reader may have just been misreading the tags, so I played around with t55xx commands until I managed to get it right. I will try to duplicate the process in my spare time so that I have a documented solution. The good news is that it does work. Now what to do with these 19 extra fobs. 🙂
