Today I migrated the DC540 website to an overseas VPS. Somehow an overseas VPS, with just 2GB of RAM, responds faster by multitudes than shared hosting at Hostgator. I guess Hostgator has reached maximum oversubscription. Please let me know how YOU experience the website, and let me know if I missed any bugs. Took me longer than I should have to get the events plugin working, for stupid configuration reasons that I am too proud to admit.
TIL about john the ripper and trigraph frequencies.
I have an assignment to crack an Office password for a document. I have tried using john and hashcat with several large wordlists, and had no luck, so I decided to go all-in and just leave a Kali instance running john in incremental (brute force) mode for “as long as it takes.” It’s been two days so far.
I have it running within ‘screen’ so that I can occasionally login to the system remotely to check progress without risk of losing it. I was excited at one point yesterday seeing that it was in the middle of checking seven-character passwords, but then I checked back later and it was checking six-character passwords. This morning, five. I wanted to understand — I assumed (without doing a deep dive on the mechanics) that it would just go literally incrementally. aaaaa, aaaab, aaaac, etc. That was an incorrect assumption.
John’s incremental mode actually operates on “trigraph frequencies.” While I understand the concept of trigraph frequencies (certain sets of three characters occur more frequently than others, and this can help with decryption efforts, I have my doubts as to whether this helps in cracking passwords. Passwords aren’t always natural speech, after all.
Anyhow, it’s been running for two days now, and I’ll post about it again when it’s done just to give an idea of whether it’s successful, and if so, how long it took vs the complexity of the password.
If anyone else wants to try using similar or other methods, let me know, and I’ll send you the hash (generated by office2john). No, I can’t send you the actual document. That would be unethical.
I suppose I have to acquire this IMSAI 8080 replica someday as well.
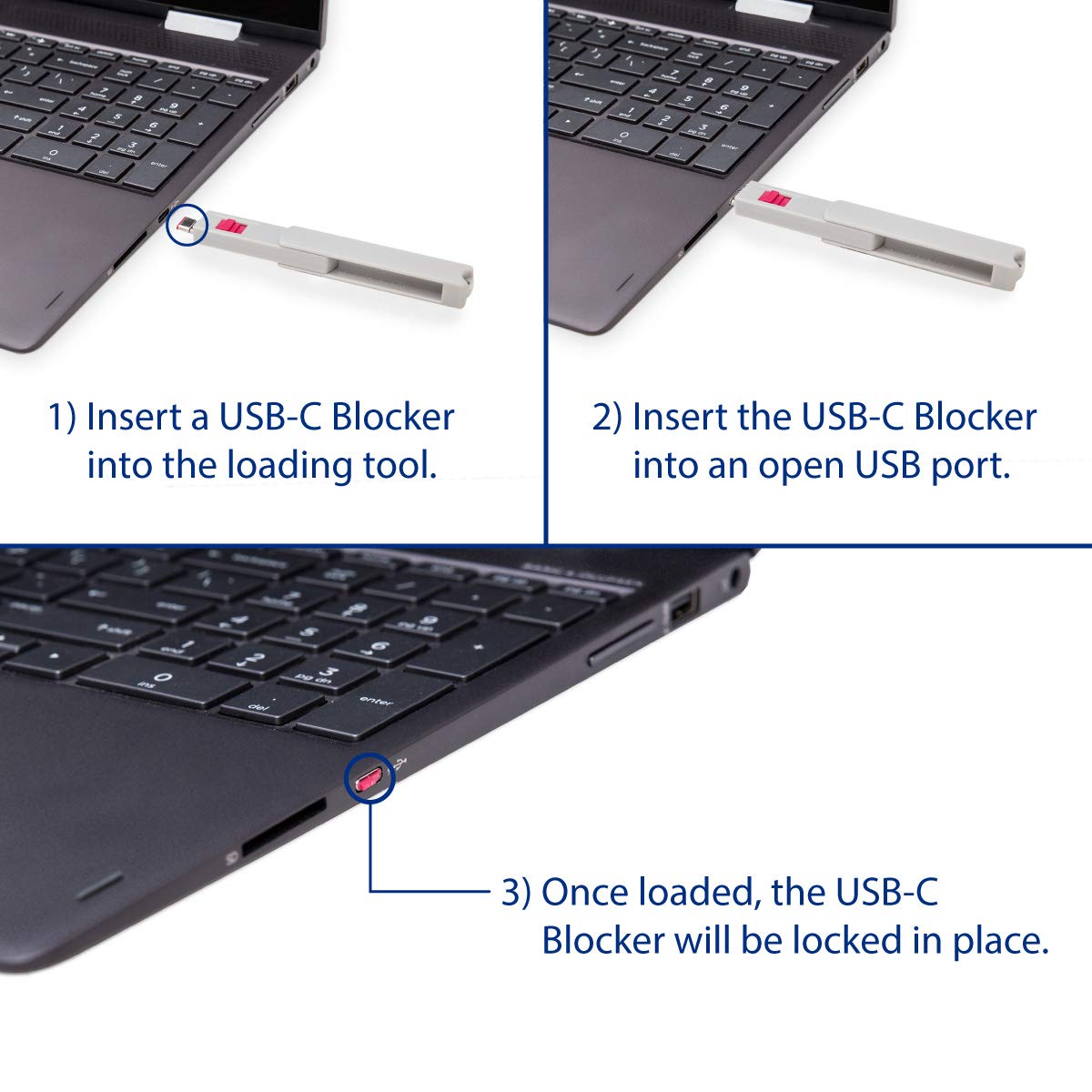
USB-C physical port blockers…
Didn’t know this existed. Sounds like a great thing for potentially hostile locations, cons, etc. Take your macbook, lock all the ports, don’t worry about somebody using USBKiller or BadUSB on you.

Holy Crap, It’s 2020!
Several people indicated being unavailable on the fourth Monday in January. Options: 4th Monday anyway, 3rd Monday (MLK day), some other day. I’ll pencil in 4th Monday anyway until we achieve consensus.
It’s been a few days now, so…
I can safely say that I believe this show will be recognized, when the rest of the world catches up and watches it, as right up there with Breaking Bad as some of the best television ever written.
Someone on Reddit posted this, and I’m really glad I didn’t have a mouthful of coffee when I saw it. Laugh with me, fellow devotees!
Apache, filebeat and Graylog – Oh My
I’ve been getting notices from one of my more popular WordPress sites of an increasing number of attempts to login lately. Compared to my other sites, this one feels like it’s being targeted for some reason. Normally I don’t pay a whole lot of attention to Apache logs unless I’m troubleshooting something, but I felt like ignoring this would be a missed opportunity.
The site is hosted on a shared site out in the wild. I don’t have full access to the server, but the vendor is kind enough to deposit apache logs into a known location on a regular basis.
So I spun up a Graylog instance at home, setup an automated rsync to suck down the logs, and then used filebeat with a logstash output to pipe them into Graylog for me. At some point I might set up a real SIEM (maybe SIEMonster’s community edition?) to do a bit of threat intel for me, but for now it’s a good pull this morning to have the logs for 20-30 websites sucked into my Graylog VM as a starter.
It’s a two-pot coffee day today.
The exercise ended up pulling in about 3 million log lines, and now I can easily visualize a history of what these ass-monkeys did on my hosting server.
FOLLOWUP: Yeah, turns out they were attracted to the WordPress by the unsecured Wiki hiding underneath. On 11/6, I upgraded mediawiki, and apparently missed turning off registrations. Since then, I’ve had 55,000 new users on the Wiki, and over 60,000 page edits (new pages, spam vandalism, etc). It was relatively easy to clean up after, but they were really having their way with that site.
I suspect the brute-forcing is going on especially hard today because they think nobody’s watching on a holiday weekend. BITCH I’M ALWAYS WATCHING.
December Meeting update…
Things are rolling right along for December’s meeting. I hope to see a bunch of you on the 16th.
- I’ve got a healthy smattering of Kali and ParrotOS workstations on the long table ready for anyone who wants to do actual pentesting against the CTF server. (These were the HP All-In-Ones I picked up at the auction.)
- The CDC book will be one door prize/raffle for one lucky winner, and I will also have a few decks of “Backdoors and Breaches,” a tabletop card-based game for simulating incident response using a D20 for other winners.
- As I mentioned before, the LED Marquee parts kits are all here ($15 a set), and I built and tested one. It’s been up and running in my family room for a couple of weeks now. If you want to assemble one at the meeting, it’s super-easy, and if you want it programmed as well, I’ll leave the choice up to you whether you want me to push the programming from my Arduino IDE on my laptop, or if you’d rather go through the process of setting up Arduino yourself, for the learning experiences. There are a number of dependencies and modifications that need to be made, more than I’ve had to do in any other Arduino project. Most of them are well-documented, and some are just common-sense fixes, I trust all of you are capable of figuring it out. It’s just a matter of do you want to go home with a working device or a challenge. 🙂
I mentioned this on Twitter, but not all of you follow Twitter — I picked up the “Crash Course Electronics & PCB Design” course on Udemy over Black Friday weekend for just $10. I can’t say enough good things about it. I have a reasonable enough basic understanding of electronics to get by on mimicry and duplication with minor troubleshooting, but I’ve always wanted a deeper understanding and more foundational knowledge. This 100-hour course, taught patiently by Andre Lamothe, is really hitting the mark.
I guess the best way to characterize it is, come for the PCB design, stay for the best approach to electronics foundational knowledge I’ve seen yet. I was going to skip ahead to the PCB design part, but I’m learning and enjoying the electronics portion so much that I haven’t been able to pull myself away. Already I’ve added a few more things to my wishlist (a signal generator, a set of thru-hole diodes, etc.) and acquired a renewed sense of vigor and enthusiasm for my portable payphone project, which fell by the wayside in the old house when I ran into issues trying to power it properly. Exciting times indeed. It’s one thing being able to troubleshoot a circuit by trial and error. It’s another thing to understand the math and theory behind it and be able to make it right — or even make it better.
Be sure to register for the meeting so that I can be sure to have enough beer chairs for everyone.
Fascinating — The Drone Databook, by Dan Gettinger
From the Preface:
Once a novelty, drones have become standard military equipment, spawning a global network of units, bases, and test sites. Battlefields in Ukraine, Syria, and Yemen, as well as zones of geopolitical conflict such as the Persian Gulf and the East China Sea, are increasingly crowded with drones of varying size and sophistication. Whether they are used for intelligence gathering, aerial strikes, artillery spotting, or electronic warfare, drones are a leading contributor to the changing character of modern war.
The Drone Databook is a study of military drone capabilities. It is comprised of profiles of 101 countries in seven regions – Asia and Oceania, Eurasia, Europe, Latin America, the Middle East and North Africa, North America, and Sub-Saharan Africa – as well as two appendixes that address military drone infrastructure around the globe and the technical specifications of more than 170 drones currently in use by these countries. The Databook evaluates the military drone capabilities of each country in terms of six categories: inventory and active acquisition programs, personnel and training programs, infrastructure, operational experience, aircraft research and development programs, and exports.
CSD-Drone-Databook-WebYou’re Not Clever: Password Patterns Exposed
Maybe you were reluctant to get on the password manager bandwagon. Passwords are inherently dangerous. Storing them in the cloud, you worry about breaches, you worry about losing access, etc. So you devised a clever pattern you thought would help you weather the storm until we finally get rid of passwords forever.
Maybe your password is a common word, then the first few letters of the site name. Long enough to avoid being guessed via brute force, and complex enough as well.
And that’s worked well for you for the past few years. You’re sitting pretty and haven’t been breached in a widespread attack.
YET.
Here’s the thing — when you use a pattern approach, every breach puts you more at risk, exposing your pattern. So far the bad actors have only been brute forcing using the breach lists (that we know of). It’s only a matter of time, if they haven’t started already, that they start cross referencing your user accounts from the various breach lists to get a per-user password list. Once that happens, inspecting those subsets for patterns will be trivial, and they will own ALL of your accounts.
Get out now, while you can. MFA where possible, long phrases if MFA is not available, 16-character complexity when long phrases don’t work.
If you don’t trust cloud password managers, use something like Keepass, but keep multiple backups in a safe place in case of corruption.