Found my old TV-B-GONE, and it didn’t work. It’s been years. Decided to open it up. Two 3V coin cells inside. One of them only registered 1.4V. Replaced it, and yay, it works again. Can’t wait to take it somewhere for juvenile shenanigans again.

Found my old TV-B-GONE, and it didn’t work. It’s been years. Decided to open it up. Two 3V coin cells inside. One of them only registered 1.4V. Replaced it, and yay, it works again. Can’t wait to take it somewhere for juvenile shenanigans again.

I’ve had this bin of Dell 1850 hot-swap power supplies (AA23300) for a couple of years now. They won’t sell, because they cost more to ship than people are willing to pay for them. I’ve been reluctant to toss them. I swear I’m not a hoarder, but if all those videogames (the ones with sub-challenges involving breaking objects into their most valuable parts to reassemble into valuable objects) taught me anything, they taught me to recognize the value in objects. This is no longer a power supply I can’t use. It has potential.

I started looking into how to use these, for example, as a bench power supply. A friend used the pinout to fashion me up a quick breadboard on-off device with indicator LED. This is fine, but it’s temporary, and I tend to jostle things. I’m thinking of something more permanent.
I ran across tjintech’s RC power supply info page, which helped me start to solidify what I wanted to get from this project.
So I started looking for the connector, which is for sure an odd beast.
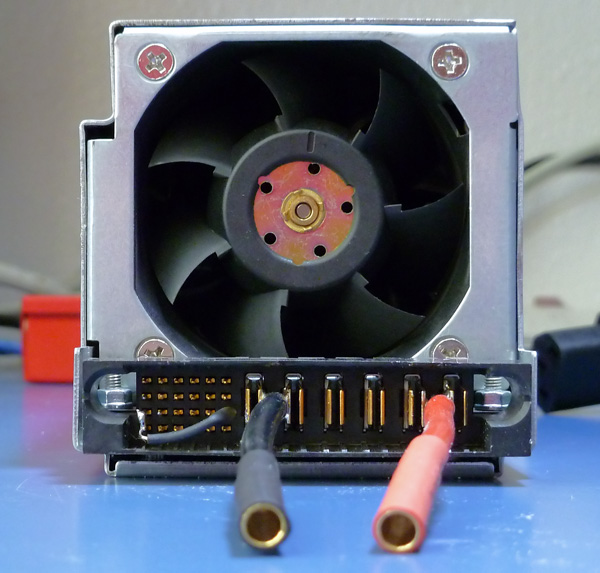
It took me a while, but I FOUND ITS MATING PLUG! It’s a TE Connectivity 6450572-1, and goes in low quantities for around $10 each.
So I started investigating the PS’ capabilities and imagining the possibilities. Right off the bat, we know it can serve 12V DC, and quite a bit of it. Those six blade connectors on the right side? Three of them are hot, and three are ground.
It would be amazing if we could also easily pull 5V off of this, but no. Many amps of 12V are at your fingertips, and 5A of 3.3V, but out of the box no 5V outs.
Other functionality includes:
So here’s the thing. I could sloppy-wire stuff directly to the board, but there’s nothing elegant or permanent about that. What if I designed a distribution unit housing, with a number of fused 12V post pairs, and then added voltage regulators to also provide 5V post pairs or even power-only panel-mount USB connectors? Or hell, even panel-mount Anderson powerpole connectors for my ham radio gear? Add switches, possibly even power meters, and Bob’s yer uncle.
Then I started looking around some more. Powerwerx has made it even easier. Look at this delicious stuff…

So now I’m thinking I could mount one of these supplies on a Pelican, mount these controls/displays somewhere, and have a simple, elegant and powerful AC to DC power solution.
Imagine being in the field, and provided one AC outlet, having the capability to power multiple radios, charge numerous phones, etc…
More to come on this one someday.
So I picked up a GoCube during its crowdfunding. I was super-excited about having a cube that could interact with a phone app, potentially play games with strangers around the world, keep track of my solve times, etc., but to be 100% honest, I was almost as excited about simply having a cube that was designed to be a speedcute.
I’d always wanted to get around to learning speedcubing techniques. I seem to have hit a wall with traditional pattern-solving techniques from the 1980s. I never solved it in under a minute that I can recall.
So I got it, played with it a while, and then forgot about it. And the thing about some devices with rechargeable batteries is that if you leave them alone too long, they die for keeps.
I came across it in a box about a week ago, thought I’d charge it up and play with it again. When you plug the USB charger in, it flashes for quite a while as if it’s charging, but then stops. And if you launch the app, it sees the cube — briefly — and then the cube goes dark and disconnects.
I googled it. A lot of people are having this issue. I tweeted about it. GoCube Support responded, said they’d make it right. However, the tweet given and the fine print taketh away. Since I’m just out of warranty (by about two months) they offered to repair it for $30 or replace it for $50. Shipping included. I figured $30 isn’t bad to get it working, but $20 more means I have one fully functional (for as long as I remember to charge it) and one that’s still a decent speedcube. So I’m waiting for that transaction to finalize.
Meanwhile, I was playing with it and caused one of the edge cubes to pop out, and decided to go ahead and disassemble as far as I could safely do so.
This is how far I got. I’m temporarily stymied on how to get further safely.

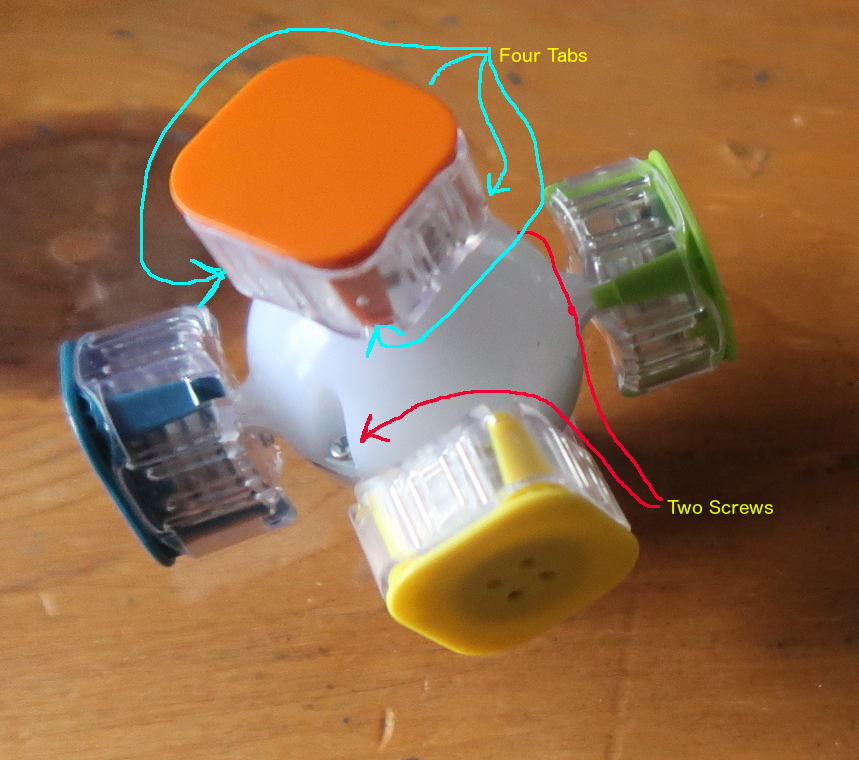
Once you get the removable cube pieces off of the skeleton, you’re left with the ball and the center pieces, which are attached to the ball in a rather ingenious manner. The ball has cone shaped tips in the six cardinal directions which shroud the turning mechanism and give the cube structural integrity.
To unlock its secrets farther, you would need to first remove the keycaps, which it seems are held in by tabs at the four corners as shown. Likely they have a custom grabby tool to remove those. Underneath that is a spring mechanism. Since the two halves of the core terminate at four points in those conical tips, even though only two screws hold the core together, you can’t open the core until you’ve removed those four center pieces.
Fortunately for our education, but not for our amateur repair, the hard work has already been done, by Intertek Testing Service. Here’s a document I found posted online. I don’t know the backstory. If you do, please enlighten me.
Until I figure out how to get the keycaps off without breaking them, I guess I’m stuck.
I started going down another path. Is it possible to revitalize a LiPo battery? The battery in the GoCube is: Rechargeable LiPo Battery; 85mAH, 0.3145 watt hours, Model: JHY661515, weight 2.1g.
I found articles indicating that a balance charger/discharger might be able to revitalize a LiPo battery. “Interesting,” I thought, and then I realized that I have one of those. I had bought it for a specialized purpose about 4-5 years ago and only used it that one time.

So then I started thinking about how I would get to the LiPo battery if I can’t get it open. The included USB charger seems pretty basic, just a molded hat with a couple of pogo-type pins that go down into the holes on one face’s center piece on the cube.


I suspect all this device is doing is shooting 5V down the holes, and there is a.tiny battery charging circuit in the core with the LiPo, so the only way my charger is going to do any good is if I can get those keycaps off of the centerpieces and open the core, so that I can bypass the device’s own recharging circuitry.
This photo is not mine, it’s from the Intertek document linked above. I’m just including it so that other explorers will know what the insides look like.
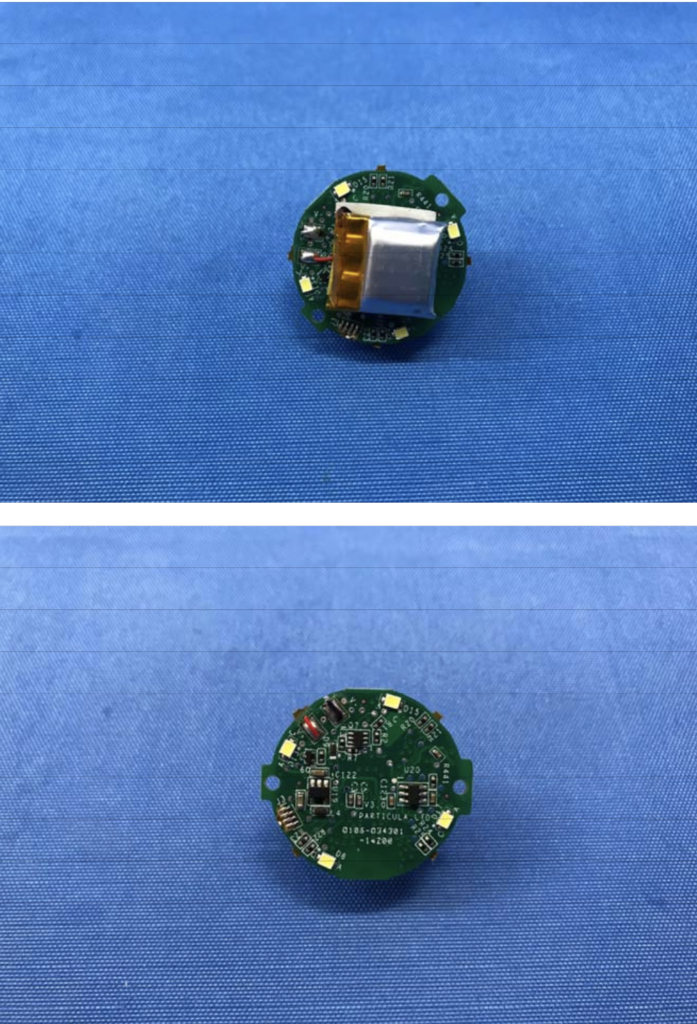
I’ll come back and edit this document if I’m able to reliably get the keycaps off and finish opening the core. This thing is nagging at me now, and I’m becoming obsessed with the idea of revitalizing it myself.
Aside from determining whether my specialized charger can revitalize that battery, I could just BUY a replacement once I crack it open. I can’t find the exact model listed above, but here’s one from Wish that looks like it will work, and for just two bucks, you can’t go wrong.
One of the most exciting talks at Def Con Safe Mode 28, for me anyway, was Cooper Quintin discussing the EFF project “Crocodile Hunter,” an SDR app that helps to discover rogue cell stations.
As some of you are aware, I spent quite a bit of time two years ago trying to get a working platform for observing 4G behavior. I had a great SDR for it, the BladeRF X40, but I never managed to get a system completely up and running.
With this release, we’ve been given a predictable, stable, working platform for 4G experimentation. The hardest part for entry-level experimenters such as myself has been automated.
My platform:
Ubuntu 20 LTS
BladeRF X40
(2) LTE paddle antennas from Amazon ($10-15)
An HP All-In-One gen 1 PC.
All that’s really required is reasonable processing power, and optimally USB 3.0. It should even run on a Raspberry Pi 4, which is wicked convenient for mobile cell tower mapping.
Caveats:
Make sure you have the 2019 BladeRF libraries, if that’s the device you use.
If you run into any problems compiling, check the issues page on the github page for the project. I ran into a couple and was able to resolve them pretty quickly.
Also, per Cooper, there’s a bug in the initial job to fetch the EARFCN list. I had to populate my config.ini manually.
We met at the local coffee shop, tried (and failed) to flash a DC26 badge, and held a mini MohawkCon.



The world of amateur consumer-grade 3D printing is fraught with challenges and opportunities for catastrophic failure.
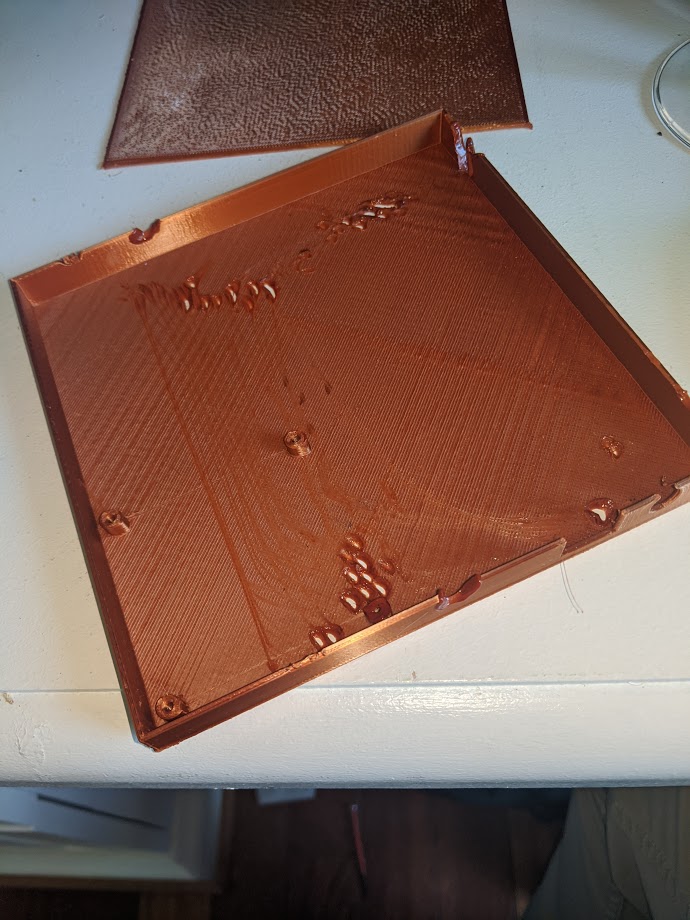
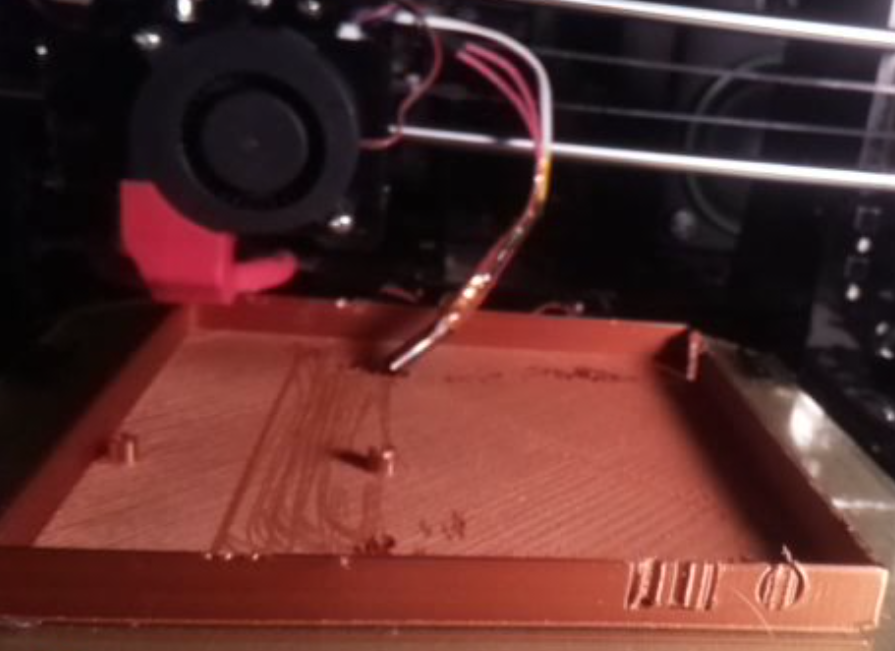
We were on a pretty good roll for a while, some good large pieces completed nicely, we got the bed leveling procedure down to a science, the system seemed pretty reliable. Unfortunately, purely mechanical systems like this (at its core, 3d printing is just motors and heaters) prefer to revert to chaos. Vibration shakes things loose, and then all bets are off.
In this case, this piece was probably 80% done when the heating element set screw vibrated loose, and then the heating element itself shook itself loose from the extruder block, and then was just dragged around on the bed by its wires until it was discovered about 15 minutes later. You can see the melted areas along the rim where it dragged over those edges repeatedly, and then the melty paths along the floor of the surface where it was simply dragged across the floor. Gorgeous, and not the quickest repair job for the printer either.
I have yet to even absorb the schedule for Def Con 28 Safe Mode. Don’t even get me started on the Million Channels of Discord. But here I am just the same, in addition to all the mental gymnastics to pump me up for this virtual con, having signed on to participate in a dynamic android debugging CTF remotely at work tomorrow afternoon.
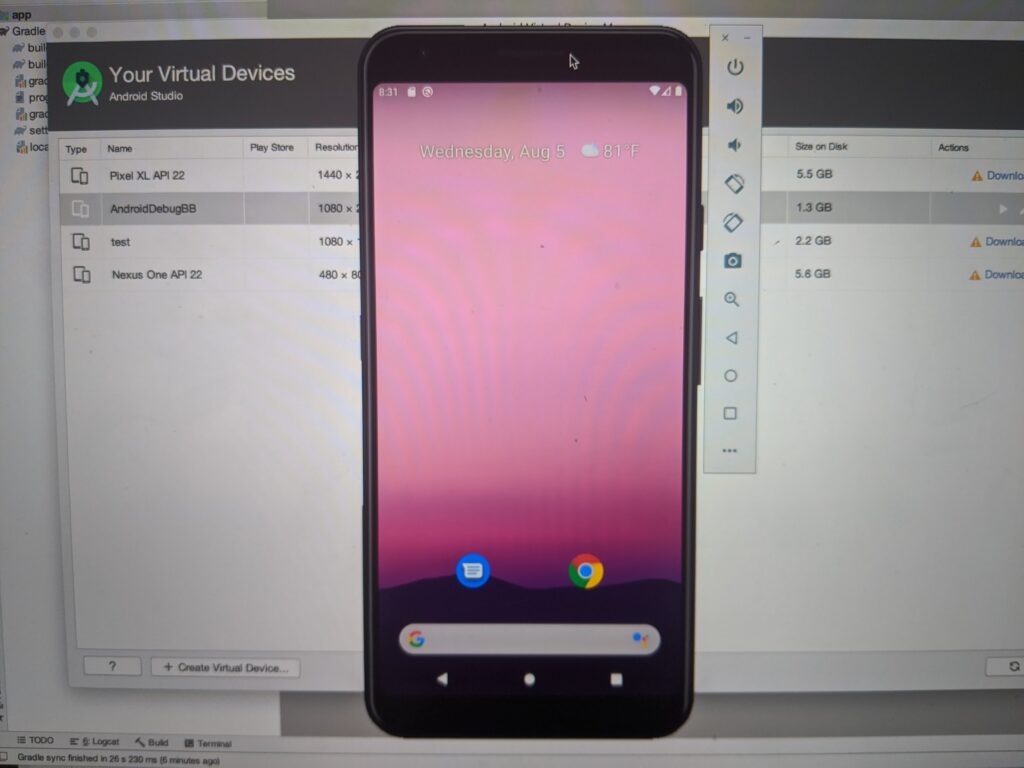
In the process of installing all of the prerequisites, I discover/remember that I had Android Studio 3.1 on this laptop 27 months ago, for. a similar CTF, my first one at this job.
Also, installing Android Studio, plugins, SDK, tools, etc., makes a MacBook Pro a bit… WARM.
WOOHOO, I have a working Pixel 3a XL emulator!
My plan is to stay home from work on Thursday the 6th and Friday the 7th, and be as fully immersed in DCSM28 as I can be. It’s been an important part of my life these past few years, and I refuse to just pretend it’s not happening, or “skip a year.” It’s obviously going to be a very different experience this year than in prior years, so I’m staying open to that experience.
To that end, I’m planning on monitoring the DC540 Discord throughout the event, while participating in whatever ways reveal themselves.
Please feel free to join in if you’re so inclined.
Are y’all playin’ EvilMog’s MUD yet?
I bought some used Def Con USB sticks on ebay. They contain official presentations. I didn’t buy them for the presentations, though — those are available online on Def Con’s media site. I bought them because they are pretty cool Def Con branded swag.
Since I won three separate auctions (DC27, DC26, and one from Blackhat), I got a refund from the seller for a combined shipping discount. When I saw the seller’s name, I did a double-take.
I just bought USB sticks from one of the most well-known hackers on the planet.
This should be fun. And not scary at all.
