I recently blogged about obtaining Chinese UID-writable magic backdoor Hello Kitty MIFARE fobs to test cloning HF RFID cards. My hope was that I’d be able to clone my kid’s college card, so she wouldn’t have to dig out a card every time she enters a space, just use a fob on her keyring, just like I cloned my LF HID card to a fob for work.
At the time I ordered them, she was away at school, so I had no way of knowing what format her card was. If her student card was MIFARE, I’d probably have a fighting chance. I believe I have successfully cloned MIFARE cards. I say I believe, because I don’t have access to a testing platform until my next hotel stay.
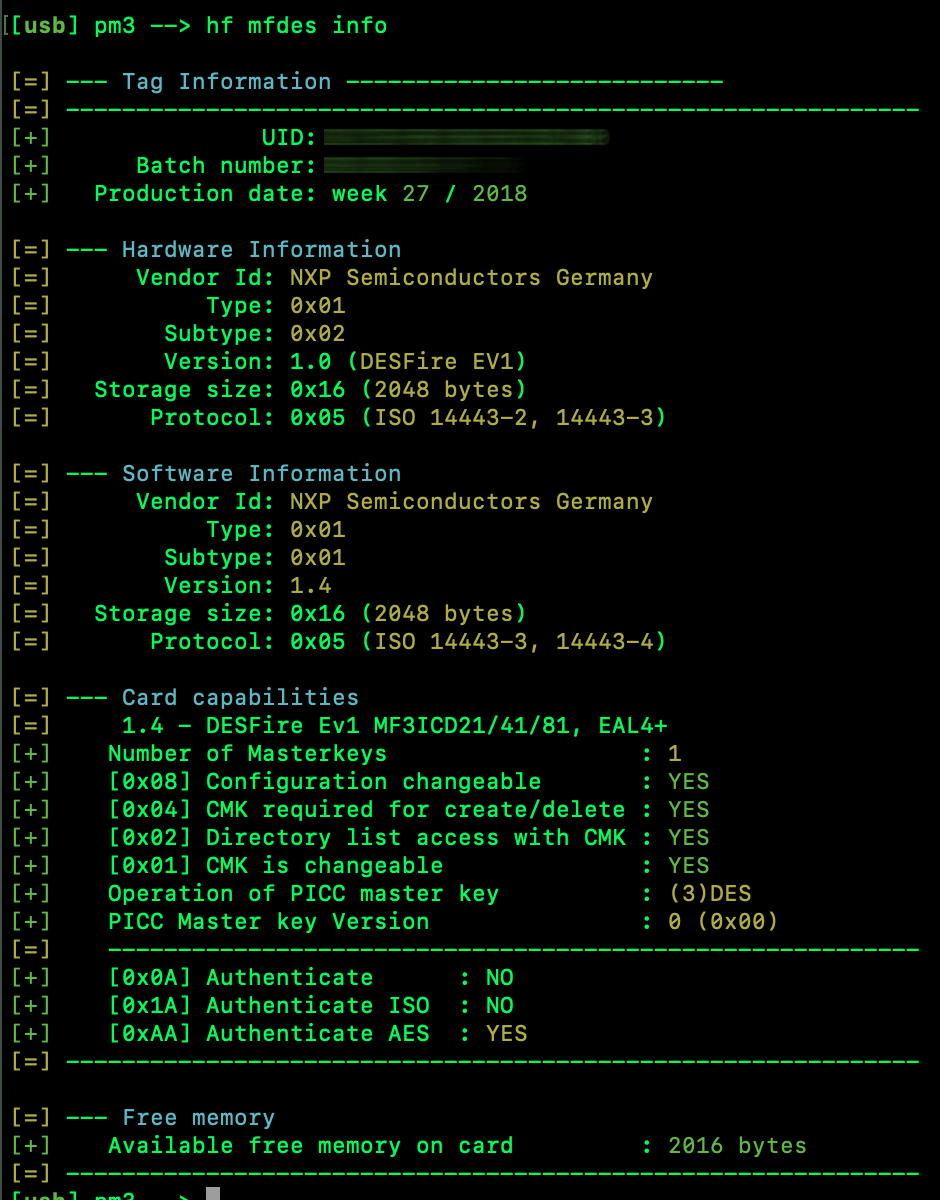
Alas, it seems like schools (at least her school) are a bit ahead of the RFID game compared to hotels. Rather than simple MIFARE, it’s DESFire EV1 2K, and from the searching I’ve been conducting tonight, it doesn’t seem like DESFire has been cracked as far as retrieving the master key. DESFire EV1 is not bleeding edge, though. According to MIFARE, it’s not recommended for new designs. Instead, MIFARE recommends DESFire EV3.
In any case, it’s a hell of a lot of fun to learn the ins and outs of the various formats, protocols, etc., and how these cards and readers work.
I’ll keep on it on the sideburner. I suspect if I do nothing and someone cracks it, it will make its way into the PM3 firmware rather quickly.
I did read something on the forums indicating that the master key might be derived through side-channel attacks involving response speed.